
Industrie 4.0 has sparked tremendous interest in connectivity, raising the possibility of enterprise-wide communications for industrial control systems. However, this complex, interconnected environment requires secure data access control management to protect against any attacks throughout the digital architecture, either accidentally or maliciously, causing severe damage upon personnel, equipment, infrastructure and the organization.
The FDT Group, an international, non-profit corporation providing an open standard for enterprise-wide network and asset integration, is supporting the new era of automation by making it easier to access information in plants and facilities with multi-generational assets that use one or multiple communication networks. The organization is also focused on incorporating methodologies and workflows into its standard based on emerging security requirements.
To meet the growing concerns of infrastructure security related to role-based management of critical information, FDT® (IEC 62453) plays a crucial part in access control and authentication. The technology was developed and designed with security measures in mind, and provides the vital building block methodology and infrastructure elements that address data access control to millions of facilities and plants empowered by FDT-enabled systems, supported by FDT FRAME™ applications (FDT/FRAMEs™) and devices employing FDT Device Type Managers™ (FDT/DTMs™). Today, this installed base already reaps the benefits of role-based security features of DTMs that help provide security for human machine interfaces (HMIs).
In this article, we will specifically discuss role-based security management evolution within the FDT standard as it relates to next-generation of automation supporting the Industrial Internet of Things (IIoT) and Industrie 4.0
The FDT Group’s legacy standard, FDT 1.2, released in 2001, includes provisions for role-based security for industrial automation systems and applications. It specifies a uniform user management model with predefined access rights for specific types of users. The standard identifies four user levels: planning engineer, maintenance engineer, operator and observer. Access control privileges for these various levels are determined by the DTM. Thus, specific sensitive functions of the FDT/DTM or the FDT/FRAME are only accessible to authorized users.
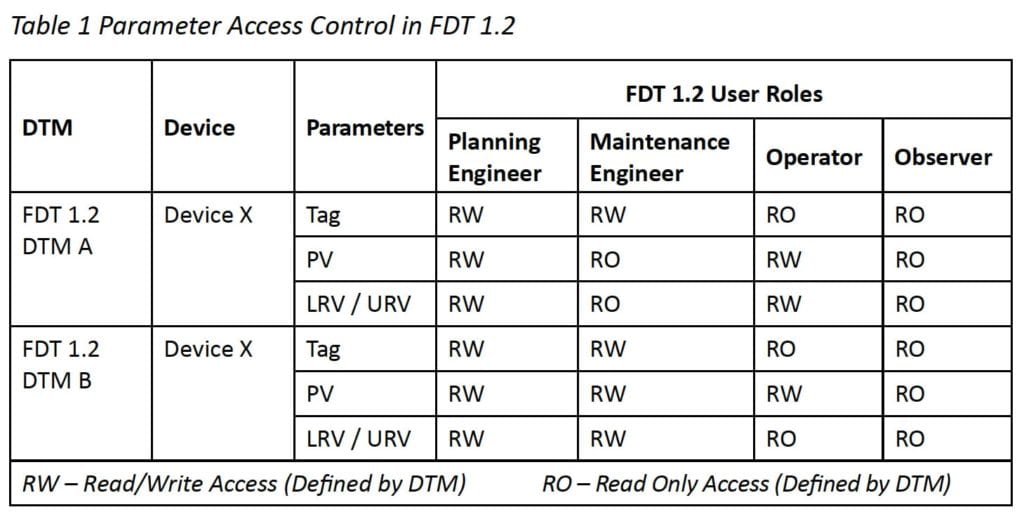
FDT technology provides clear guidance for DTM HMIs, and has continued to evolve to keep pace with market requirements for enhanced security features. However, there remains certain limitations in the context of field device parameters. FDT 1.2 normally doesn’t provide functionality to configure parameter accessibility for different roles. For instance, an operator can configure LRV/URV for a given device using one DTM, but can’t perform the same operation with another DTM without the required access approval. The access control permission is totally defined by the DTM. Table 1 shows the example of this scenario.
 The current FDT 2.0 standard, issued in 2012, incorporates bolstered security capabilities, including more granular DTM security with enhanced user rights and privileges added to the security settings. The predefined levels of security have been replaced with a user-defined capability, which allows industrial facilities to define who can have access to certain items – putting the level of security into the hands of the user.
The current FDT 2.0 standard, issued in 2012, incorporates bolstered security capabilities, including more granular DTM security with enhanced user rights and privileges added to the security settings. The predefined levels of security have been replaced with a user-defined capability, which allows industrial facilities to define who can have access to certain items – putting the level of security into the hands of the user.
With FDT 2.0, user levels are simplified to three levels: engineer, observer and expert. Similar to FDT 1.2, the engineer has a full permission set and the observer has a reduced permission set. However, the expert category provides access control capabilities and functions that are enhanced by allowing system engineers to configure the accessibility of DTM functions and parameters using the FDT/FRAME application. This provides more control for the systems. FDT/DTMs may be integrated in different FRAMEs, which may have varying access requirements. They may restrict visibility and accessibility of devices and some data. Restrictions can be established to provide plant safety or to present customized views for different users. The FRAME can easily be used to configure the desired access control settings for any expert. The privilege of the functions and data can be changed, depending on where the DTM is used or which operational phase is active. For instance, an expert user may have full control when the plant is being configured or upgraded, but changes to devices may be restricted when the plant is in production state.
Additionally, an expert may have different permissions for a single device and DTM when the device is connected in the plant or in the device lab. In the device lab, the user may have all the necessary authorizations to calibrate or commission the device. Minimal changes may be allowed when the instrument is connected later to the actual running control system.
In a nutshell, the privileges of data access and function invocation are configurable via the FRAME based on the plant operational state, individual user or team experience, and other factors. Table 2 shows some example scenarios.
At the August 2017 FDT A&S Working Group meeting, there was a presentation of an access control prototype that proved the FDT 2.0 access control capabilities. The prototype also demonstrated that access control can be tailored according to specification needs. In the prototype, an engineer could easily set up and configure the expert’s accessibility via the customized FDT/FRAME. Furthermore, the engineer could configure the role-dependent access rights of DTM HMIs.
Expert users could only operate on the functions or modify the parameters allowed by the engineer. In this case, FDT 2.0 provides flexibility to the user to configure parameter access rights. For instance, expert users can commission LRV/URV for Device X using DTM C or DTM D, as long as the right to access that parameter is granted by the engineer. Table 2 illustrates an example of this scenario.
 To summarize, the FDT Group is at the forefront of the new era of automation, supporting a comprehensive, open architecture for the connected world of industrial automation networks and assets. Ongoing advancement of FDT technology is leveraging major developments like the IIoT and Industrie 4.0 to enable end users to realize the true potential of decentralization, interoperability and integration. It is also providing robust, user-defined security capabilities that enable industrial sites to take control system security measures into their own hands.
To summarize, the FDT Group is at the forefront of the new era of automation, supporting a comprehensive, open architecture for the connected world of industrial automation networks and assets. Ongoing advancement of FDT technology is leveraging major developments like the IIoT and Industrie 4.0 to enable end users to realize the true potential of decentralization, interoperability and integration. It is also providing robust, user-defined security capabilities that enable industrial sites to take control system security measures into their own hands.
The current version of FDT employs a standardized access control facility and infrastructure. With proper implementation by all vendors, FDT/DTMs can allow users to carry out a wide range of commissioned actions. Roles can be easily created, changed or discontinued as the needs of the plant or industry evolve. Data can be more securely protected by setting varying access levels for different user roles. Centralized administration can effectively reduce management cost. With these technologies, FDT has created a more connected, integrated and secure industry automation service, which can be very valuable to customers.
Authors:
Jason Chan Sin Wai
– member of FDT Group Architecture & Specification working group
Sham Wai Rock
– member of the FDT OPC-UA project group